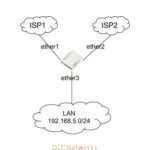
We got a question from students, how the DDOS attack looks like? are they similar to probing attack? In this article, we will talk about it and monitor the attack with the MikroTik router. In order to observe, we need to set up a network topology that allows us to see all packets that are flowing on the network, by having a central point as the main connection hub, it gives us better observability as inbound and outbound traffic will go through the same place, not scattered through different links.
In order to observe, we need to set up a network topology that allows us to see all packets that are flowing on the network, by having a central point as the main connection hub, it gives us better observability as inbound and outbound traffic will go through the same place, not scattered through different links.
Now, let’s talk about the tools we are using.
The first tool we can use to monitor the traffic flows is the firewall connection. It has a filter where you can use it to focusing on a particular connection like the picture below:
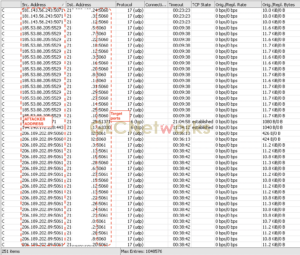 the picture above tells us the attackers tried to probe which IP address running services on port UDP:5060/5061. this port number is commonly used for SIP (Session Initiation Protocol) service. In fact, only 1 server is running SIP service, but the attackers tried to access SIP port on other IP addresses as well, which makes these activities suspicious. Some SIP service require authentication (for example username and password), therefore, it is most likely they also do brute force attacks on that, trying to login using common usage of username and password.
the picture above tells us the attackers tried to probe which IP address running services on port UDP:5060/5061. this port number is commonly used for SIP (Session Initiation Protocol) service. In fact, only 1 server is running SIP service, but the attackers tried to access SIP port on other IP addresses as well, which makes these activities suspicious. Some SIP service require authentication (for example username and password), therefore, it is most likely they also do brute force attacks on that, trying to login using common usage of username and password.
The second tool we gonna use is torch, which is able to displays traffic flows on a particular network interface. see picture below as an example:
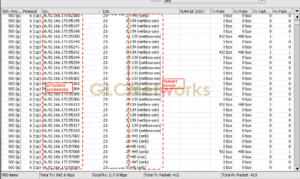 as you see above, the attacker is trying to probe TCP:139/445 port, the legendary port for Windows SMB services that is well-known for many security issues, including wannacry. The attackers may launch a brute-force attack on the service or execute an exploit to them. Unpatched (old version) SMB services can be exploited by attacker and the computer can be controlled remotely.
as you see above, the attacker is trying to probe TCP:139/445 port, the legendary port for Windows SMB services that is well-known for many security issues, including wannacry. The attackers may launch a brute-force attack on the service or execute an exploit to them. Unpatched (old version) SMB services can be exploited by attacker and the computer can be controlled remotely.
What about DDOS? DDOS (Distributed Denial Of Service) is an attack where attacker generate lots of request/traffic to a target. The request is so many until your server cannot handle, make the server resources busy (CPU, RAM, harddisks), therefore it will reject later request (denial of service).
Ok, so now i know that my network/servers are under attack, what next?
Well, some ideas of what you can do:
- Record the IP address of attackers for further action like blacklist, blocking, redirecting, etc
- Analyse the IP address
- Report IP address to external coordination body, for example CERT (Computer Emergency Response Team). Usually every country has their own CERT organisation, run by government or public fund.
- Put a dedicated box which will do attack analyses and enforcing (for example: drop the connection)
Thank you for reading
the topic above is part of our training. To get more information, please contact us here.