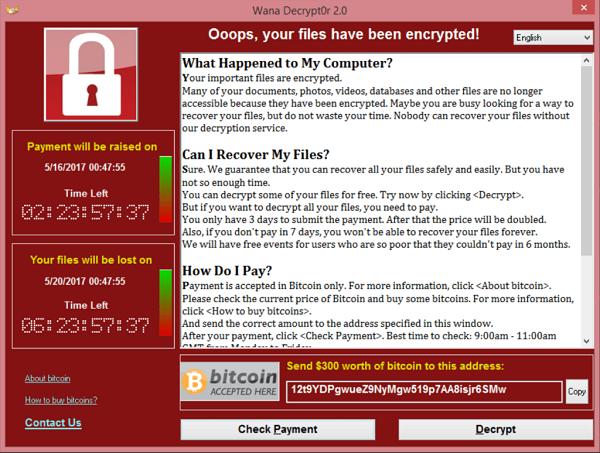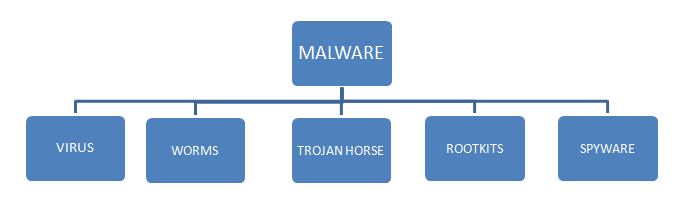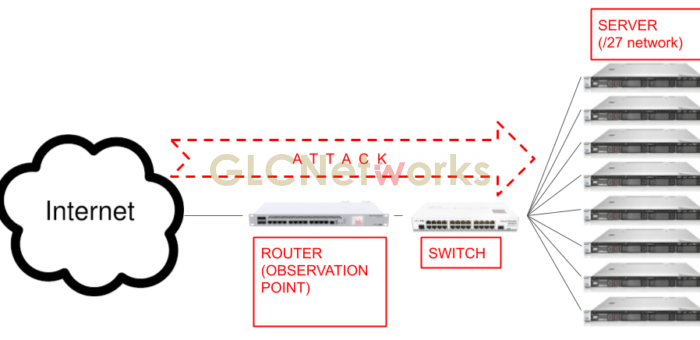
Observing the DDOS/probing attack with Mikrotik device
We got a question from students, how the DDOS attack looks like? are they similar to probing attack? In this article, we will talk about it and monitor the attack with the MikroTik router. In order to observe, we need to set up a network topology that allows us to see all packets that are flowing on the network, by having a central point as the main connection hub, it gives us better observability as inbound and outbound traffic will go through the same place, not scattered through different links. Now, let's talk about the tools we are using. The first tool we can use to monitor the traffic flows is the firewall connection. It has a filter where you can use it to focusing on a particular connection like…