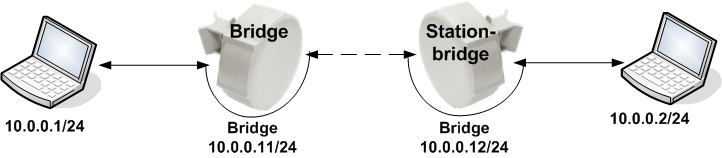
Connecting 2 remote places using wireless bridge
So, somebody asked me about a topic about "connecting 2 remote places using wireless bridge". so he has 2 rooms (or office) separated by a road, each location already has its own network, and then the plan is to connect them. as simple as that. lets make this process to be systematic and logical way. first of all, we need to gather requirements and current condition. here are the check lists: Current conditions both sites have computer network already running, and both network use network id of 10.0.0.0/24 both sites is separated by a road and the distance is around 30 meters both are located in second floor Requirements: to connect both sites using wireless connect using mikrotik devices if possible, donot change the current configuration max traffic between 2 sites can…